Captive Portal, Guest WiFi, Splash Pages. What is it all about?
While Captive Portals are one of the most largely extended technologies across businesses and organizations worldwide, many people still don’t know what they are, how they work, or what benefits they can bring.
If you are one of them and you want to learn more about Captive Portals, this article is for you!
In simple terms, a Captive Portal is a web page or Splash Page that is displayed to newly connected users before they are eventually granted broader access to a network’s resources.
Captive Portals are commonly used to present a logging or landing page that may require payment, authentication, acceptable user policy – also known as EULA – or other valid credentials that both the network user and the host have to agree on.
They can be found on a wide range of mobile and pedestrian broadband services, including business hotspots and commercially provided WiFi — like in coffee shops, airports or malls. Additionally, captive portals can be used to access residential wired networks like apartments and hotel rooms, not forgetting other enterprises like business centers.
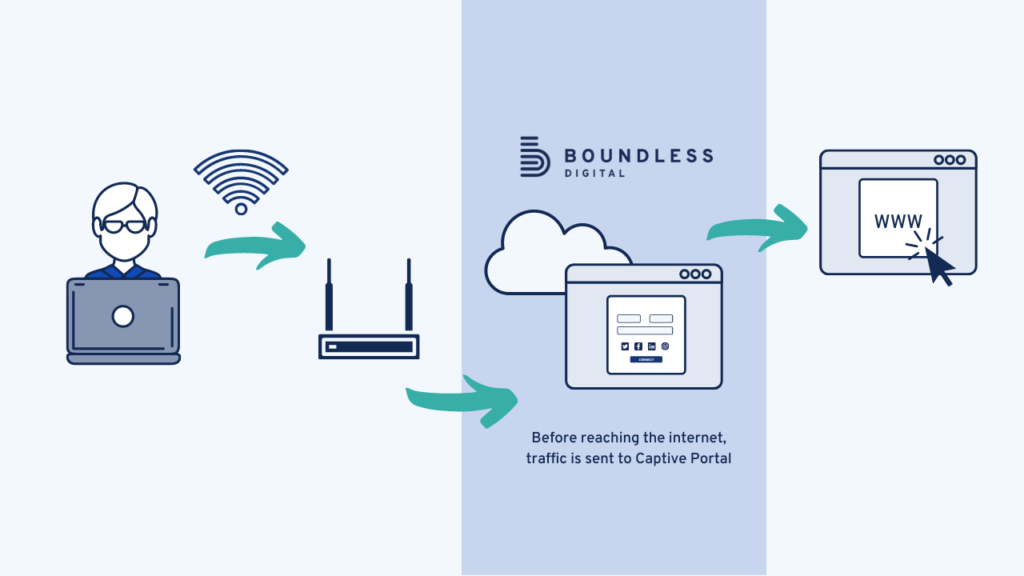
The Captive Portal’s Splash Page feature users from being granted broader access to the network they are trying to connect to until the host has established verification.
For example, when a client enters a specific physical location with a smartphone, they will be prompted to join a secure and free network connection via the guest WiFi network through various login methods.
When that happens, a captive portal is automatically displayed through the default browser on the smartphone. This portal will then request the client to key in personal information to access the internet service through this access point. If, in any case, the network detects that the client has connected to the system earlier, they may be able to bypass the landing page.
Get unlimited access to Boundless Guest during 14 days – for free.
A captive portal is typically used in an open wireless network. A welcome message usually is displayed, showing the clients the requirements to access the system. The conditions may include things like the allowed ports or liability.
Captive Portals are primarily used for communication purposes and marketing. Typically, access to the internet is restricted over the open WiFi until the client fills out a registration form. In doing so, they exchange personal data. This form will appear when they open a web page or automatically appear when they join the network.
This is where the name “captive” is born, as users cannot freely use the internet services until they accept the terms and conditions.
Sometimes the service is also called social WiFi as it may ask clients to join using their social media accounts like Facebook or LinkedIn. This makes it a powerful marketing tool.
This can be done by a couple of steps that include selecting your SSID. SSID is the name that is usually given to a wireless network, which makes it easier to search and connect to it. If you do not have an SSID, you will have to create one.
Next, you will have to configure the Walled Garden. The Walled Garden lists all restricted sites that the guest client cannot access unless they go through the page. Additionally, you can choose the desired redirection page.
When using Captive Portals, you can get access to additional functionalities and customizations. For instance, you can set the connection time for each device to avoid clogging up the system. Additionally, you can also set the bandwidth limitation for a device, limiting the amount of data used in a particular time frame.
Creating a Splash Page is key step when setting up your Captive Portal.This can be done through the integrated builder included in your solution. Some solutions offer more advanced Splash Page builders than others.
When designing your Splash Page, or Login Screen, you can choose to either add a consent message, activating automatic translation, and, in some cases, even adding a paid access button if you wish to monetize the internet connection.
If you want to make your Splash Page look more professional, you can choose to add a company logo, add text, or customize the theme to make it look more attractive and professional.
Modern captive portals solutions come with a myriad of options to log in and win internet access.
Nowadays, the most popular login authentication types are email address, SMS, Active Directory, and social login. The last one consists of using a visitor’s social media accounts as a single-sign-on (SSO) to connect to the Guest WiFi Network. Frequent social network providers are Facebook, Twitter, or LinkedIn.
Hackers usually take advantage of free Guest Wi-Fi connections to steal information from unsuspecting wireless users. The protection of users is hence very crucial. This can be done by choosing different login methods particular to the business needs, like seen above.
Moreover, it is strongly recommended to add an advanced DNS-based web-content filter to protect your guest WiFi network from unwanted online threats.
Finally, this is the last stage that involves collecting and analyzing the clients’ login information. This data provides businesses with qualified leads for their marketing efforts, as well as quality data to build more customized campaigns.
Cloud-based Captive Portals allows you to manage your Guest Wi-Fi networks remotely. With controller-based solutions, on the other hand, the captive portal must be controlled on the premise.
Cloud-based portals allow network administrators to efficiently manage the Guest network via the cloud, check the portal’s status, and even troubleshoot remotely. The cloud will enable administrators to also react to problems right away when issues arise. As a result, IT managers can simplify and streamline the management of their Guest Wi-Fi.
Cloud-based solutions also dramatically reduce the cost of implementing and managing captive portals and allow for more scalable growth.
If you are looking for a Captive Portal solution to implement on your business, you may want to start by defining your core needs. To help you with that, here are a few questions you can ask yourself:
Answering these questions will help you define the features you may need. Not all Captive Portals offer the same functionalities. Also, not all solutions are compatible with all vendors! So you should make sure the solution you choose is the most adapted to your needs. Have a look at our guide to chose the best Captive Portal solution for your needs.
If you need a secure, flexible and cloud-based Captive Portal solution for your business, Boundless Guest may be a match! Here is some product information if you want to have a look.
And if you are interested to learn more about Enterprise-grade Captive Portal solutions, reach out to our team!
1207 Delaware Ave #552, Wilmington, Delaware 19806
Americas: +1 (347) 464-6510 - EMEA: +33 (0) 181 22 12 80

We are proud to announce the launch of our new brand identity, marking a significant milestone in our evolution. This rebrand reflects our commitment to continuous innovation, agility, and automation — always moving forward.